
 | Basics on How a Encryption Algorithm Works |
Encryption is the method of modifying information with an formula, known as a cipher, making it un-readable to just about anyone other than those having specific knowledge, generally known as a key. The kind and length of the keys used rely upon the particular encryption formula as well as the degree of security necessary. In conventional encryption just one key is. The outcome of this is called encrypted data. The opposite of this task and to produce the encrypted data understandable again, is known as decryption. In several contexts, the term encryption could also implicitly make reference to the opposite method and can generally furthermore execute decryption.
The goal of encryption is to protect the data as it is transferred from point-A to point-B via a network. Typically the network can be a wireless devices like phones, routers, satellite signals and can include even wired devices like ISDN, T1 or cable modem. Encryption can protect the confidentiality of messages and information being transferred.
The goal of encryption is to protect the data as it is transferred from point-A to point-B via a network. Typically the network can be a wireless devices like phones, routers, satellite signals and can include even wired devices like ISDN, T1 or cable modem. Encryption can protect the confidentiality of messages and information being transferred.
 |
Here is the basic on how an encryption algorithm works:
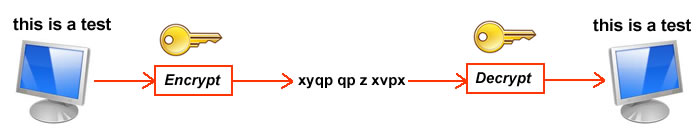
Lets take the words: this is a test
not this contains the letters "t","h","i","s","e" and "a".
Lets substitute the letters as follows: x=t, y=h, q=i, p=s, v=e and z=a
This is what we call an encryption "key" or formula. Your web browser calls it a "security certificate". That is what web browsers use as the "key" when sending sensitive information over the web like credit card transactions.
The sentence now looks like: xyqp qp z xvpx
Now there are two sides, a sender and a receiver. Before the sender sends out the sentence, it encrypts it using the example. Once it is being sent through the airways, it is sent as xyqp qp z xvpx. One the receiver receives the encrypted text, it then uses the key to restore the message back to its original form this is a test
Now this was a simple example. Today's computer encryption is much more complicated. Generally there are two types of encryption, symmetric encryption and asymmetric encryption. Each of these types use different algorithms to produce encrypted text to send. In symmetric encryption, the formula divides up data into small pieces called blocks.
It then switches letters around, changes the information in each block into numbers, compresses and expands the data, and runs those numbers through different math formulas that include the key. Then the process repeats over and over a specified number of times. Now you really have it encrypted. An example of the above of swapping the digits into blocks would be hsit si a etst. so it is swapped 2431 21 1 2431. Now, if we apply the letter swapping it would now look like this: ypqx pq z vxpx
A asymmetric encryption algorithm, in comparison, deals with the text as if it were an extremely big number, raises it to the power of some other very big number, and after that computes the remainder right after dividing it by using a 3rd very large number. Eventually, the remainder number is changed back to text. Security applications are able to use the identical algorithms in different ways, which is the reason the recipient must use the exact software to decode the information which you employed to encode it. Now I won't attempt to encrypt my tiny sentence using asymmetric encryption but you get the idea.
In the world of programming, there is one other technique use and this is called hashing. Hashing is a form of security which is slightly different from encryption. Where encryption is a two step process used to first encrypt and then decrypt a message, hashing condenses a message into an irreversible fixed-length value, or hash. Two of the most common hashing algorithms seen in networking are MD5 and SHA-1. SHA is considered more secure than MD5. SHA is the "Secure Hash Algorithm" and is one of a number of cryptographic hash functions published by the National Institute of Standards and Technology.
Hashing is used only to verify data; the original message cannot be retrieved from a hash. When used to authenticate secure communications, a hash is typically the result of the original message plus a secret key. Hashing algorithms are also commonly used without a secret key simply for error checking. So once it is encrypted, that is it... you cannot go back. A good typical use for this is to store passwords in a database to protect against hacking. Even if the hacker saw the encrypted password, he will not able to retrieve what it was. The only way to unlock the password is to guess or change it.
Well, I hope that this explains a bit on how encryption and encryption algorithms work.
Lets take the words: this is a test
not this contains the letters "t","h","i","s","e" and "a".
Lets substitute the letters as follows: x=t, y=h, q=i, p=s, v=e and z=a
This is what we call an encryption "key" or formula. Your web browser calls it a "security certificate". That is what web browsers use as the "key" when sending sensitive information over the web like credit card transactions.
The sentence now looks like: xyqp qp z xvpx
Now there are two sides, a sender and a receiver. Before the sender sends out the sentence, it encrypts it using the example. Once it is being sent through the airways, it is sent as xyqp qp z xvpx. One the receiver receives the encrypted text, it then uses the key to restore the message back to its original form this is a test

Now this was a simple example. Today's computer encryption is much more complicated. Generally there are two types of encryption, symmetric encryption and asymmetric encryption. Each of these types use different algorithms to produce encrypted text to send. In symmetric encryption, the formula divides up data into small pieces called blocks.
It then switches letters around, changes the information in each block into numbers, compresses and expands the data, and runs those numbers through different math formulas that include the key. Then the process repeats over and over a specified number of times. Now you really have it encrypted. An example of the above of swapping the digits into blocks would be hsit si a etst. so it is swapped 2431 21 1 2431. Now, if we apply the letter swapping it would now look like this: ypqx pq z vxpx
A asymmetric encryption algorithm, in comparison, deals with the text as if it were an extremely big number, raises it to the power of some other very big number, and after that computes the remainder right after dividing it by using a 3rd very large number. Eventually, the remainder number is changed back to text. Security applications are able to use the identical algorithms in different ways, which is the reason the recipient must use the exact software to decode the information which you employed to encode it. Now I won't attempt to encrypt my tiny sentence using asymmetric encryption but you get the idea.
In the world of programming, there is one other technique use and this is called hashing. Hashing is a form of security which is slightly different from encryption. Where encryption is a two step process used to first encrypt and then decrypt a message, hashing condenses a message into an irreversible fixed-length value, or hash. Two of the most common hashing algorithms seen in networking are MD5 and SHA-1. SHA is considered more secure than MD5. SHA is the "Secure Hash Algorithm" and is one of a number of cryptographic hash functions published by the National Institute of Standards and Technology.
Hashing is used only to verify data; the original message cannot be retrieved from a hash. When used to authenticate secure communications, a hash is typically the result of the original message plus a secret key. Hashing algorithms are also commonly used without a secret key simply for error checking. So once it is encrypted, that is it... you cannot go back. A good typical use for this is to store passwords in a database to protect against hacking. Even if the hacker saw the encrypted password, he will not able to retrieve what it was. The only way to unlock the password is to guess or change it.
Well, I hope that this explains a bit on how encryption and encryption algorithms work.